Understand the real mechanics of SPF, advanced syntax, and how to troubleshoot the toughest issues. Written for IT professionals and anyone serious about email security.
What Is SPF and Why Does It Matter?
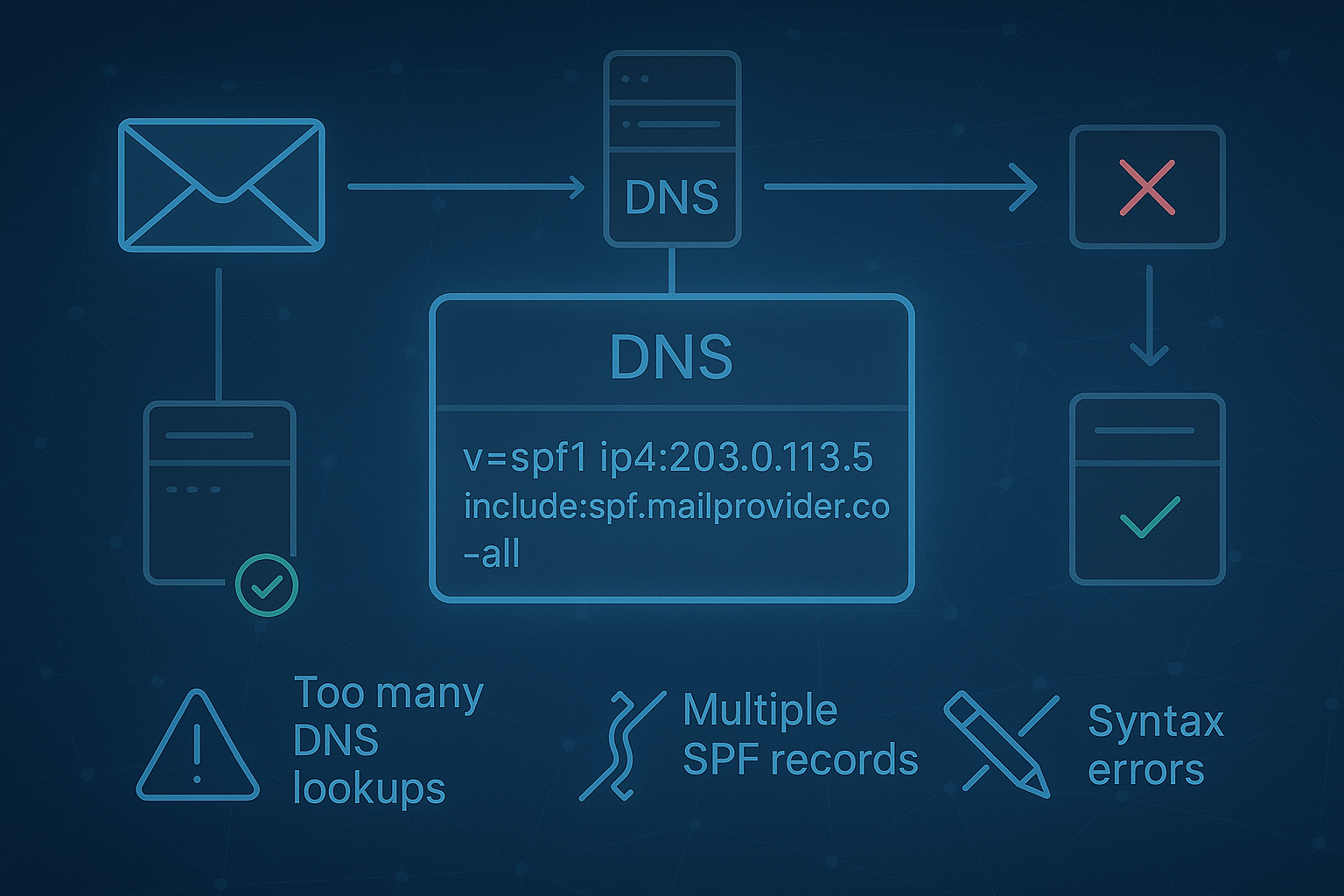
SPF (Sender Policy Framework) is a DNS-based email authentication protocol. It lets you specify which mail servers are allowed to send emails on behalf of your domain. When a receiving mail server gets a message, it checks your domain’s SPF record to see if the sending server’s IP is on the list. If it is, the email passes SPF. If not, the server may reject, flag, or quarantine the message. This helps stop spoofing and phishing attacks, and improves your email deliverability.
SPF is one of three core authentication pillars, alongside DKIM and DMARC. While DKIM adds a cryptographic signature and DMARC ties everything together with policy and reporting, SPF is the first line of defense-especially against IP spoofing and unauthorized senders. Learn more about the basics in our SPF, DKIM & DMARC Explained post.
How SPF Works Behind the Scenes
When you send an email, the recipient’s mail server performs these checks:
- It extracts the domain from the
MAIL FROM(Return-Path) address. - It queries DNS for a TXT record starting with
v=spf1for that domain. - It compares the sending server’s IP address to the mechanisms in the SPF record.
- Based on the result, it applies the policy: pass, fail, softfail, or neutral.
If the IP matches an allowed sender, the email passes SPF and moves on to the next authentication step. If not, the server can block, flag, or send the message to spam. SPF is especially important for passing BIMI and VMC checks, which display your brand logo in recipients’ inboxes-if SPF fails, your logo won’t show up [source].
SPF Record Syntax: The Advanced Stuff
An SPF record is a DNS TXT entry. Here’s a breakdown of advanced syntax:
v=spf1 ip4:203.0.113.5 include:spf.mailprovider.com -allv=spf1: Identifies the record as SPF.ip4:ouip6:: Authorizes specific IP addresses.include:: Authorizes another domain’s SPF record (useful for third-party senders).all: The default catch-all. Preceded by a qualifier:-all: Hard fail (reject unauthorized senders).~all: Soft fail (mark as suspicious).?all: Neutral (no policy).
You can also use a, mx, and exists mechanisms, and redirect= for advanced delegation. For a full syntax guide, see Cracking SPF Records: Basic to Advanced Syntaxes.
SPF in Action: What Happens When You Send an Email?
- You send an email from your mail server.
- The recipient’s server checks the
MAIL FROMdomain. - It looks up the SPF record in DNS.
- If the sending IP is listed (directly or via
include:), SPF passes. - If not, SPF fails, and the server applies your policy (reject, flag, or allow).
This process is invisible to end users but critical for keeping your emails out of spam and stopping attackers from impersonating your domain [source].
Common SPF Pitfalls and How to Troubleshoot
SPF is simple in theory, but real-world setups can get messy. Here’s how to troubleshoot the most common issues:
- Missing senders: If you forget to include all your sending services (like marketing platforms, CRM, or website forms), their messages will fail SPF. Always update your record when adding new senders [source].
- Multiple SPF records: Only one SPF record per domain is allowed. Merge all mechanisms into a single record to avoid failures [source].
- Too many DNS lookups: SPF allows a maximum of 10 DNS lookups. Exceeding this limit causes a “permerror,” and SPF will fail. Use tools to check your lookup count and consolidate
include:statements where possible. - Syntax errors: Typos, extra spaces, or bad mechanisms will break your record. Use an SPF validator to check your syntax before publishing.
- Overly permissive records: Allowing too many IPs or using
+allmakes your SPF useless. Keep your record as restrictive as possible [source]. - Forwarding issues: SPF breaks when emails are forwarded, because the forwarder’s IP isn’t in your record. DMARC and DKIM help mitigate this.
For a step-by-step troubleshooting guide, see our SPF Troubleshooting Guide.
Best Practices for Bulletproof SPF
- List every legitimate sending service in your SPF record.
- Use
-all(hard fail) for strong enforcement, or~all(soft fail) if you’re still testing. - Keep your record under 255 characters and avoid exceeding 10 DNS lookups.
- Regularly audit your SPF record as your infrastructure changes.
- Combine SPF with DKIM and DMARC for layered protection.
- Test using online SPF checkers after every change.
- Don’t allow large IP ranges unless absolutely necessary.
For a full deliverability audit, consider our Audit complet de délivrabilité des e-mails service.
Independent Research: SPF Weaknesses and Real-World Data
Large-scale studies show that while SPF adoption is growing, many domains use weak or misconfigured records. About one-third of domains allow emails from over 100,000 IP addresses, making them vulnerable to spoofing. Around 2.9% of records contain outright errors or ineffective rules. Researchers recommend keeping SPF records as restrictive as possible and regularly auditing for errors [source].
“A significant number of domains have very permissive SPF configurations. For example, 34.7% of domains allow emails to be sent from over 100,000 IP addresses, making it easier for malicious actors to spoof email senders and conduct phishing.” – BIFOLD, TU Berlin
For more, see the full research paper.
FAQs: Advanced SPF (WordPress Format)
What happens if I have more than one SPF record?
Only one SPF record is allowed per domain. Multiple records cause SPF to fail. Merge all mechanisms into a single record.
How do I fix “SPF Validation Failed” errors?
Check for typos, extra spaces, or unsupported mechanisms. Use an online SPF checker to validate your record before publishing.
Why do forwarded emails fail SPF?
Forwarders use their own IP addresses, which aren’t in your SPF record. Combine SPF with DKIM and DMARC to improve results.
What’s the difference between -all and ~all?
-all is a hard fail (reject unauthorized senders). ~all is a soft fail (mark as suspicious but still deliver).
How do I keep my SPF record under the 10 DNS lookup limit?
Limit the use of include: mechanisms, and avoid unnecessary DNS lookups. Use SPF flattening tools if needed.
Where can I get a full deliverability audit?
Mail Fortifier’s Complete Email Deliverability Audit covers SPF, DKIM, DMARC, and more.
For more on SPF and email authentication, see Cracking SPF Records: Basic to Advanced Syntaxes, Google’s SPF Troubleshooting Guide, and our SPF, DKIM & DMARC Explained post.
Tags: SPF, email authentication, troubleshooting, deliverability, DNS